[ Wednesday, March 30, 2022 ]
Chapter 9: Privacy, Security,
and TCS (3 rules; 3 digit transaction numbers)
As initially noted above, the
HIPAA statute itself is a bit of a hodgepodge, with 5 separate Titles covering
everything from actual insurance portability to health savings accounts to, of
course, health information privacy and security. But when we talk about HIPAA, we’re really
talking about a subtitle of Title II known as “administrative simplification.”
Adminsimp, as we like to call
it, is mainly composed of 3 separate components (there we go with the number 3
again): the “Transactions and Code Sets Rule,” which standardizes the form,
format, and content of specified electronic transactions in the healthcare
industry; the “Privacy Rule,” which establishes a set of rules and standards
for the protection of the privacy of an individual’s health information; and
the “Security Rule,” which establishes minimum requirements for protecting the
security of that information.
As discussed above, one of the
motivating factors of HIPAA (after addressing “job lock” caused by actual
insurance portability, as the name implies) was the twin goal of improving the
efficiency of the healthcare system by increasing the amount and ease of
electronic transactions. This meant
determining some specific transactions that happen over and over in the
industry, finding a way to convert those transactions into electronic data
interchange transactions, and standardizing those electronic transactions so
that they would become more popular, easier, and ubiquitous.
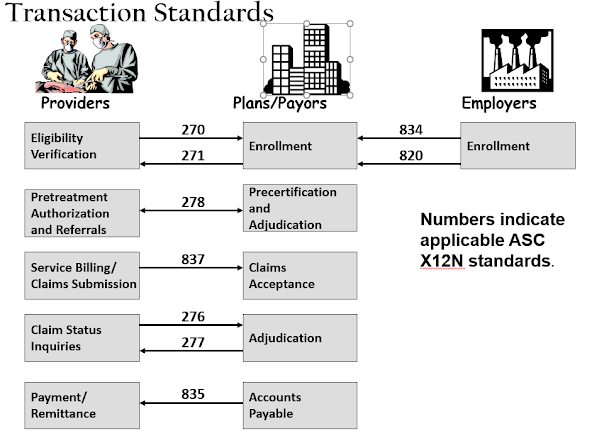
There are a total of 9
transactions that were targeted and standardized, several of which are
reciprocal. To perform the
standardization, HHS turned to the American National Standards Institute, which
does everything from standardizing the size or light bulbs and electric plugs
to shipping containers. The standardized
transactions represent exchanges of information between providers and payors,
and between insurers and employers, and are each signified by an ASC X12
number, as shown here:
Prior to HIPAA, each health plan had a slightly different form that providers had to fill out to submit a bill electronically. They were all roughly based on the standard billing form used by Medicare for its electronic billing, but each had some differences, which meant that providers either needed more staff to do the billing and complete the different forms for each payor, or had to hire a healthcare clearinghouse to do the translation for them. Since HIPAA now requires that covered entities use these forms when conducting these transactions, the cost and inefficiency of different standards should be reduced. Of course, it’s not really as easy as that: there are still supporting documentation, pre-authorization and post-claim reviews, and the like (surely you understand that payors make money if they can delay claims even a little bit). But the goal was certainly admirable, and almost certainly has been beneficial overall.
The Transactions and Code Sets
Rule, as you can see, is really a technical rule. If you engage in these specific transactions in
electronic format, you have to do so in the prescribed forms. As we’ll see below, the Privacy rule is more
of a cultural/administrative rule: it changes the way healthcare businesses
operate by requiring the adoption of a culture of privacy with respect to
patient information. The Security rule
is really a little of both – it’s mostly about implementing specific safeguards
(or more accurately, safeguards addressing specific matters) and meeting
technical requirements, but it’s also about the way things are done.
As for the specifics of the
Privacy Rule and the Security Rule: well, they deserve their own sections,
below.
Jeff [5:02 PM]